Here, I will briefly explain What is CRC SHA and will add some methods by which you can remove CRC SHA from the context menu in Windows 10.
Windows 10 has introduced us to a lot of new features and components. Some of these were totally new unknown, and even their names had no clue about what they do. In this post, I will tell about one such component. You must have seen an entry named CRC SHA in the Context Menu (Right-click menu) if you are a Windows 10 user and has installed 7-Zip on your computer. Majority of the users have no idea what CRC-SHA is, and what it does. Yet a lot of people are eager to learn to remove CRC SHA from the Context menu.
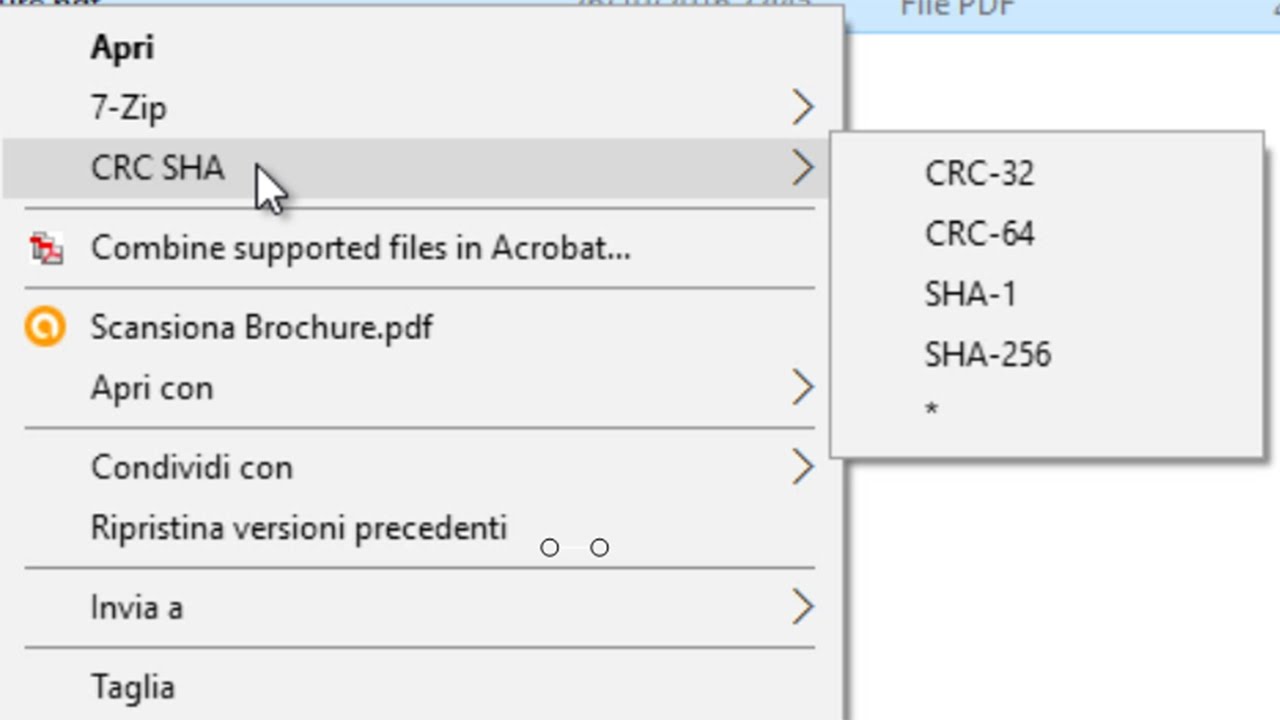
What is CRC SHA?
If you are using a Windows 10 PC and have 7-Zip installed on your system, you must have noticed that an entry CRC-SHA is added automatically to the Context menu. This entry is present alongside the 7-Zip options. When you point the side arrow, it displays, CRC-64, SHA-256, SHA-1, CRC-32, and * entries.

Basically, CRC stands for Cyclic Redundancy Check. It is employed in digital networks for checking/identifying any changes made to the data. On the other hand, It’s complimentary component, SHA is an abbreviated form of Secure Hash Algorithm. Its potent use is in determining the integrity of data downloaded from the Internet, ensuring it is not corrupted. There are some other options too, like CRC-64, SHA-256, SHA-1, and CRC-32. CRC and SHA both are security algorithms. If you want to learn further about CRC and SHA, read the next section. However, if you don’t want to get deep into details, just skip to the method to remove CRC-SHA from the Context menu in Windows 10.
What is CRC?
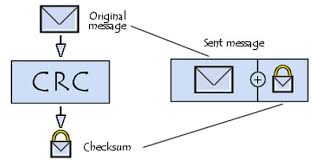
A cyclic redundancy check (CRC) is an error-detecting code commonly used in digital networks and storage devices to detect accidental changes to raw data. Based on the remainder of a polynomial division of their contents. On retrieval, Blocks of data entering these systems get a short check value attached. The calculation is repeated and, in the event the check values do not match, corrective action can be taken against data corruption. CRCs can be used for error correction.
CRCs are so called because the check (data verification) value is a redundancy (it expands the message without adding information) and the algorithm is based on cyclic codes. CRCs are popular because they are simple to implement in binary hardware, easy to analyze mathematically, and particularly good at detecting common errors caused by noise in transmission channels. The function that generates it is occasionally used as a hash function because the check value has a fixed length.
The CRC was invented by W. Wesley Peterson in 1961. The 32-bit CRC function of Ethernet and many other standards is the work of several researchers and was published in 1975.
Courtesy: Wikipedia
What is SHA?
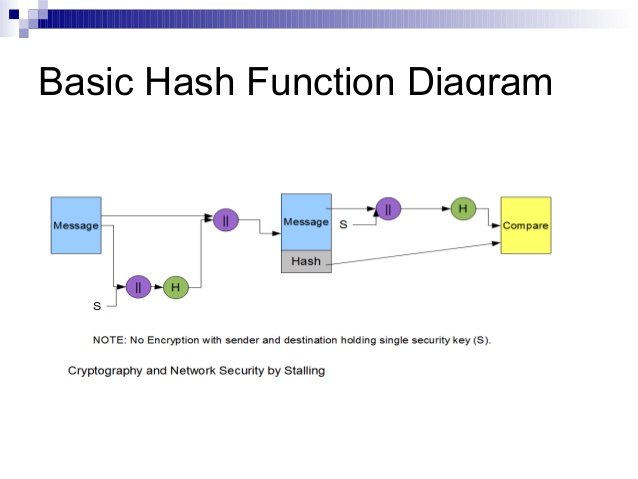
The Secure Hash Algorithms or SHA are a family of cryptographic hash functions published by the National Institute of Standards and Technology (NIST) as a U.S. Federal Information Processing Standard (FIPS), including:
- SHA-0: A retronym applied to the original version of the 160-bit hash function published in 1993 under the name “SHA”. It was withdrawn shortly after publication due to an undisclosed “significant flaw” and replaced by the slightly revised version SHA-1.
- SHA-1: A 160-bit hash function which resembles the earlier MD5 algorithm. This was designed by the National Security Agency (NSA) to be part of the Digital Signature Algorithm. Cryptographic weaknesses were discovered in SHA-1, and the standard was no longer approved for most cryptographic uses after 2010.
- SHA-2: A family of two similar hash functions, with different block sizes, known as SHA-256 and SHA-512. They differ in the word size; SHA-256 uses 32-bit words where SHA-512 uses 64-bit words. There are also truncated versions of each standard, known as SHA-224, SHA-384, SHA-512/224, and SHA-512/256. These were also designed by the NSA.
- SHA-3: A hash function formerly called Keccak, chosen in 2012 after a public competition among non-NSA designers. It supports the same hash lengths as SHA-2, and its internal structure differs significantly from the rest of the SHA family.
The corresponding standards are FIPS PUB 180 (original SHA), FIPS PUB 180-1 (SHA-1), FIPS PUB 180-2 (SHA-1, SHA-256, SHA-384, and SHA-512). NIST has updated Draft FIPS Publication 202, SHA-3 Standard separate from the Secure Hash Standard (SHS).
Courtesy: Wikipedia
How to Remove CRC SHA from the Context Menu in Windows 10?
All of us casual Windows users find this entry unwanted and useless in the Context menu. Therefore, we need to remove it from the Context menu. So that when we right-click, we don’t have to see this entry in the menu and only important entries are present there. You have come to the right place. I will explain how to remove CRC SHA from the Context menu in Windows 10 in the simplest manner.
GUIDE: Hide/Remove CRC SHA from the Context menu
Follow these steps in order to remove CRC SHA from the Context menu in Windows 10:
Step-1: Firstly, go to Search bar and open 7-Zip from there (type 7-Zip in the Search bar, and then press Enter).
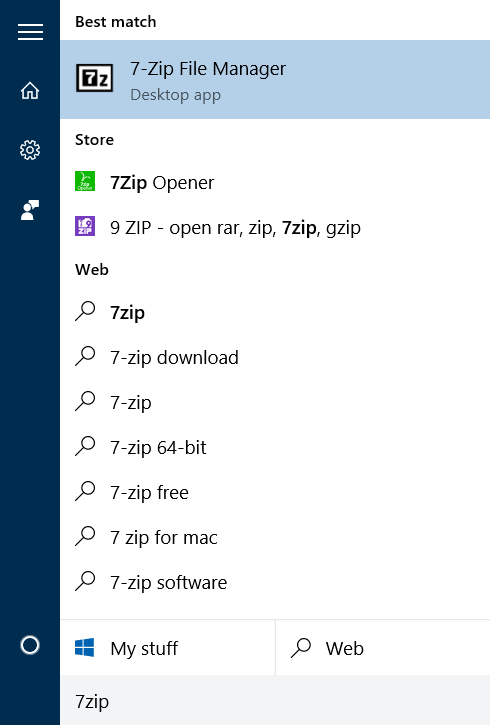
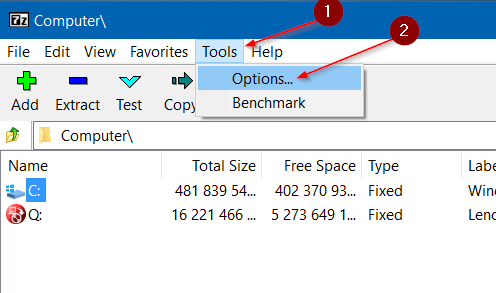
Step-2: After opening, click on Tools present on the upper bar on your screen. Next, click on Options.
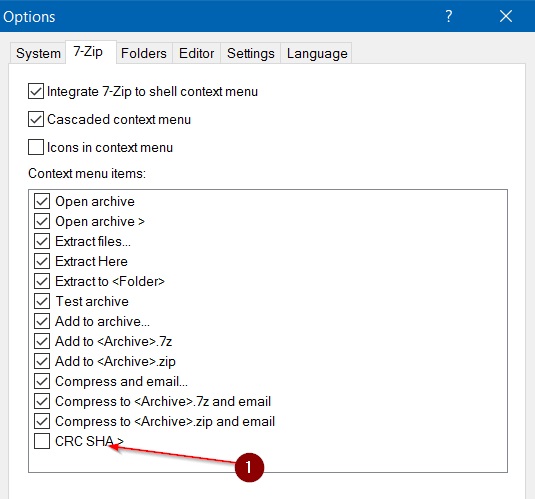
Step-3: Now switch to the 7-Zip tab. Uncheck the checkbox CRC SHA present under Context menu.
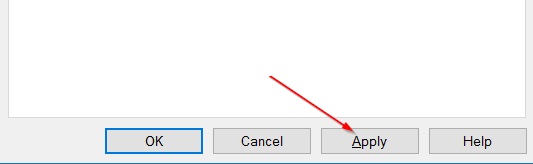
Step-4: Finally click on Apply and then Ok.
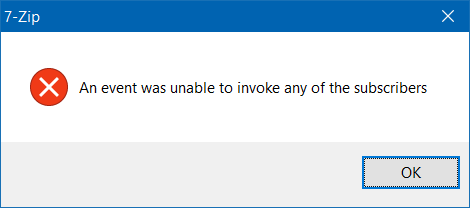
Note: A warning dialog box will pop up with this message, “An event was unable to invoke any of the subscribers.” Just click on OK to remove the context menu entry.
Done. That’s all you have to do to remove the unwanted CRC SHA from the Context menu.
Conclusion
CRC SHA is an entry that came along with 7-Zip in Windows 10. Majority of the users have no idea about what this is. The entry is indeed not so wanted and can be removed from the Context menu. The method to remove CRC-SHA from the Context menu is really simple and easy. For any queries, doubts or suggestions, feel free to visit the Comments section.
Hope I helped you to get rid of the unwanted CRC-SHA from the Context menu in Windows 10.
